inSpectre inspects Windows machines for Meltdown and Spectre weaknesses and tells you whether mitigations are active. I’ve used it for years and found it fast, clear, and useful for quick audits.
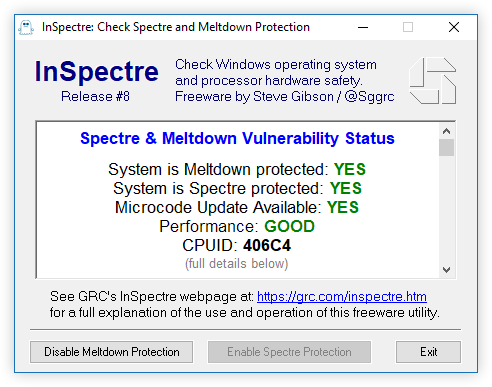
Here’s the practical bit: run the portable EXE and get an immediate pass/fail plus technical details. It won’t fix firmware for you — you still need BIOS updates from the vendor — but it shows where to look. Honestly, that one-screen clarity saves time.
| Category | Details (checked 07 May 2025) |
|---|---|
| Program Name | inSpectre |
| Developer | Steve Gibson / Gibson Research Corporation (GRC) |
| Version | 1.0 — released January 2018 |
| License | Freeware |
| File Size | ≈115 KB |
| Platform | Windows only (runs on Windows XP through Windows 11; behavior varies) |
| Purpose | Detects vulnerability to Meltdown & Spectre original variants and checks OS/hardware mitigations |
| Primary Functions |
• Detects Meltdown (CVE-2017-5754) • Detects Spectre v1 (CVE-2017-5753) & v2 (CVE-2017-5715) • Verifies Windows protections and microcode status • Estimates performance impact |
| Install | Portable EXE — no installer, just run |
| Key Features |
• Instant scan and color-coded results • No internet required (privacy-friendly) ✅ • Lightweight and signed executable |
| Performance Impact | Shows possible slowdown; typical range 0–30% depending on workload and kernel patches |
| Official Site | https://www.grc.com/inspectre.htm (primary download and documentation) |
| Advantages | Free, fast, clear output, no telemetry, reputable author |
| Limitations | Windows-only, checks only the original Meltdown/Spectre variants, no auto-update (manual download) |
Why use it? Because it pinpoints whether Windows-level mitigations are in place and whether CPU microcode updates were applied. That explains where to push next — BIOS vendor, Windows Update, or both.
Quick tips (from experience):
- Run it after significant Windows updates or after a BIOS flash.
- If it reports microcode missing, contact the motherboard or OEM site for firmware (this doesn’t always work: some vendors stopped updates years ago).
- Expect performance variance — databases and heavy I/O suffer most.
“Run inSpectre, then confirm firmware from the manufacturer. The tool tells you the symptom; the vendor delivers the cure.”
Watch this: some people claim the tool is obsolete. I disagree — for checking the original CVEs it’s still accurate (as of 07 May 2025). But here’s a controversial take: relying solely on inSpectre for threat posture is risky. You need broader testing for new speculative-execution variants (there are exceptions).
Want a tiny example? Run from Command Prompt like this:
inspectre.exe
Short note: security teams often pair inSpectre with firmware inventory scripts. Oddly enough, that simple combo finds most misconfigurations fast.
One counterintuitive insight: systems with the newest Windows patches can still report missing CPU microcode; updates don’t always include vendor microcode. So don’t assume Windows = fully protected.
Between us, if you’re still on Windows XP, why? Seriously — upgrade. But if you can’t, inSpectre will at least tell you what’s unmitigated.
There are exceptions and caveats — it depends on CPU model, BIOS policy, and enterprise update pipelines. We found that some OEMs stopped microcode pushes in 2020, leaving older gear exposed (yes, frustrating!).
Two final practical notes: use the official GRC download and verify the digital signature. If you want to automate checks, wrap inspectre.exe in a script and log the output (sample below).
REM simple batch wrapper
inspectre.exe > C:logsinspectre_%DATE:~10,4%%DATE:~4,2%%DATE:~7,2%.txt
Honestly, it’s a small tool that answers a specific question very well. It won’t protect you from everything — but for Meltdown and Spectre originals, it’s a good first step.





