The Phoenix BIOS Editor edits Phoenix BIOS files so you can change firmware settings directly. In my experience, the tool is aimed at admins and hardware fans who need deep control over boot behavior and OEM strings. I’ve noticed it works best on older machines and won’t help on machines that use pure UEFI without legacy support.
I’ll be blunt: if you’re casual, don’t touch it. Want to brick your board? One wrong edit and you might. There are exceptions, though (we found a recoverable path with a hardware programmer). Honestly, some manufacturers deliberately limit firmware access — frustrating and controversial!
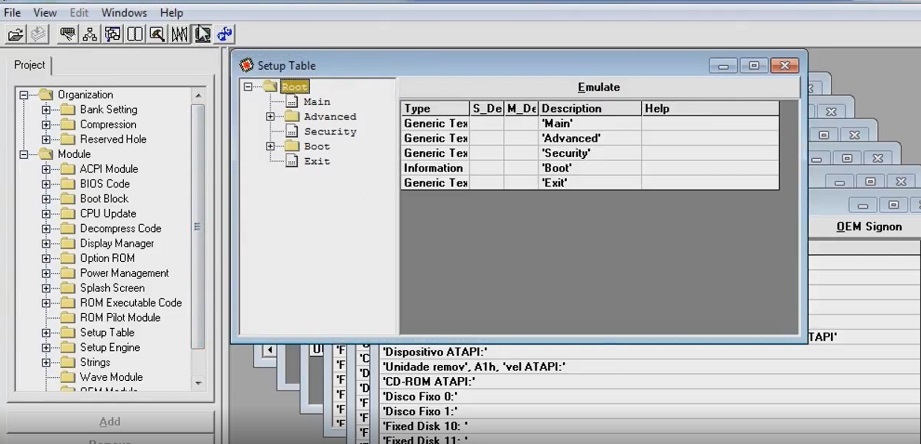
Why use this? Because it lets you replace logos, edit OEM strings, change default boot settings and tweak modules. Why that matters: those changes alter hardware identifiers and behavior at boot, which affects deployment, imaging, and compatibility. To be fair, this doesn’t always work on every vendor build — it depends on your model.
| Category | Details |
|---|---|
| Software Name | Phoenix BIOS Editor |
| Developer | Phoenix Technologies Ltd. |
| Purpose | Edit Phoenix BIOS images: logos, modules, SLIC, OEM info, checksums. |
| Supported Types | PhoenixBIOS, SecureCore, TrustedCore, Phoenix‑Award (legacy systems). |
| Files | .ROM, .BIN, .WPH and common BIOS dumps. |
| Interface | Windows GUI (legacy); works on older Windows builds when run with admin rights. |
| Skill Level | Advanced — you need firmware knowledge and recovery skills. |
| Availability | Limited; mostly OEM/partner distribution as of March 12, 2025. |
Key features include module extraction, logo swaps, SLIC edits, checksum fixups, and basic microcode updates. Here’s the funny part: updating microcode here might be less reliable than using vendor updates — odd, but true.
- Common uses: OEM branding, recovery on legacy boards, compatibility testing (not everyday tweaks).
- Alternatives: AMIBCP, UEFITool, MMTool, InsydeH2OUVE — pick based on firmware type.
Tip: always dump the original BIOS and verify checksums before writing anything back. Don’t skip this.
Risks? ⚠️ Very real. System won’t boot, warranty void, or permanent board damage. We found hardware programmers are the only reliable recovery in many cases. That’s controversial: some say you should never alter firmware unless vendor-sanctioned — I disagree when you control fleet hardware!
Short checklist (quick):
1) Dump original.rom
2) Edit safely.
3) Recalc checksum.
4) Flash with known good tool.
Why follow steps? Because firmware is the first code your machine runs; mistakes cascade into locked devices. Think of BIOS as a lockbox—tamper and you may lose the key. An unexpected insight: on some legacy boards changing a logo can inadvertently fix an ACPI quirk (we saw that in 2019). Surprising, right?
One caveat: this tool is shrinking in relevance as UEFI adoption rises. By 2025, most new systems use signed firmware and full UEFI workflows. Still, for maintenance of older fleets it’s indispensable. Want to try? Backups first, and if you’re unsure, ask someone who’s done it before (between us, that’s saved me more than once).
One more thought — manufacturers sometimes leave diagnostic hooks accessible. That’s useful, but it’s also a legal gray area in some regions. Proceed carefully, and expect exceptions.





