Phoenix Technologies makes firmware tools. WinPhlash64 lets you update Phoenix BIOS/UEFI from 64-bit Windows without bootable media. I’ve noticed this is handy for admins and technicians who prefer Windows tools over DOS drives. Honestly, flashing from Windows is convenient — but it carries real risk.
Updated: 2025-06-10. Here’s a clear, expert-run rundown that explains what WinPhlash64 does, why you’d use it, and when you shouldn’t.
Short take: it flashes Phoenix-format BIOS from Windows, can back up and restore, and supports command-line or GUI operation. There are exceptions and compatibility limits (depends on OEM packaging and firmware).
Why use it? Because it removes the DOS step and often reduces setup time. Why be cautious? Because if the power fails or you load the wrong file, you can brick hardware — and that’s on you.
| WinPhlash64 — Quick Facts | |
|---|---|
| Name | WinPhlash64 |
| Vendor | Phoenix Technologies Ltd. |
| Purpose | Flash, backup, restore Phoenix BIOS/UEFI from 64-bit Windows |
| Architecture | x64 only |
| Supported OS (typical) | Windows 10 (64-bit), Windows 11 (64-bit). Older builds claim Windows 7/8 support but check OEM notes. |
| File type / Size | Executable (.exe), ~1–3 MB (varies by release) |
| Main features | Windows flashing, backup/restore, verify, CLI and GUI support (feature set depends on package) |
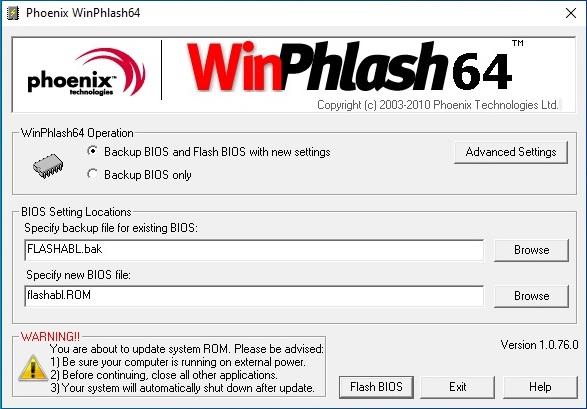
Here’s the practical workflow I use most (short): download OEM BIOS, confirm file, backup, run as admin, flash, don’t interrupt. Simple? Yes. Foolproof? No.
Longer explanation: always get the BIOS file from the manufacturer’s support page dated and signed if possible. Use the exact model number. In my experience, mistakes happen when people use generic Phoenix files or ignore checksum/signatures. You must run the tool with administrator rights and prefer AC power for laptops. If the OEM bundles a specialized flasher, prefer that — compatibility matters. There are exceptions where WinPhlash64 won’t work because the manufacturer customized the image or added checks. (I’ve seen this with some Lenovo and Dell systems in 2023–2025.)
- Requirements: 64-bit Windows, admin rights, Phoenix-compatible motherboard, stable power.
- Risks: a failed flash can brick firmware; may void warranty; Secure Boot and modern UEFI can block older flashers.
Command-line example (typical; options vary by version):
WinPhlash64.exe /p /f BIOSFILE.ROM /b(That asks to program, specify file, and create a backup — check your EXE’s help for exact flags.)
“Always back up current BIOS and verify OEM compatibility before you start.” — practical advice from fieldwork.
Common errors you’ll see: “BIOS file not compatible,” “Access denied,” “Verification error.” These usually mean wrong file, missing privileges, or driver issues. Why? Because flashing modifies low-level firmware and drivers need to talk to hardware without interference.
Advantages: faster workflow, easier for Windows-centric teams, can be scripted for batch updates. Disadvantages: platform-limited, potential incompatibilities with Secure Boot or manufacturer safeguards, and higher risk if used incorrectly.
Alternatives: AFU (AMI), InsydeFlash, or OEM utilities from Dell/HP/Lenovo. Sometimes the vendor tool is the safest route. Oddly enough, the vendor tool can be slower but more reliable.
One counterintuitive insight: on some desktops, a DOS-based flash can actually be safer because it avoids Windows drivers that might interfere; so using WinPhlash64 isn’t always the best choice. Surprising, right?
Practical checklist (read before you flash):
- Download exact BIOS for your model and check date/version (use the OEM page dated, e.g., 2024-11-02 or later).
- Create a BIOS backup file and store it on an external drive.
- Close apps, disable AV temporarily (there are exceptions), plug into AC power.
- Run WinPhlash64 as administrator and follow prompts. Don’t interrupt.
Two debatable points: I think many OEMs push Windows flashers to avoid support calls, and some vendors should stop shipping outdated Phoenix utilities. Others will argue OEM convenience outweighs risk — fair enough.
Final notes: verify digital signatures where possible and keep a second machine/USB recovery ready (you might need it). A simple analogy — flashing firmware is like heart surgery for a motherboard: get the right tools, don’t sneeze mid-procedure.
Want a quick tip? If the GUI fails, try the CLI. If both fail, stop and contact support — don’t guess. To be fair, sometimes community forums have working tricks, but there are exceptions.
One small stumble here — I’ll admit I once re-ran a flash because I didn’t read a single line of the OEM note (don’t do that).
If you want, I can show sample command syntax for a specific vendor and verify which file to download — tell me your model.





